Public Key vs. Private Key Encryption: Understanding the Key Differences
Public keys and Private keys are the two general encryption techniques in cryptography. Cryptography presents public key encryption as asymmetric encryption, and private key encryption is stated as symmetric encryption.
Both play a pretty significant role in cybersecurity. However, both show differences mainly in the way data is encrypted and decrypted.
We shall in this blog look at the differences between public key and private key encryption methods and how they work-principles and use of both methods.
What is Encryption?
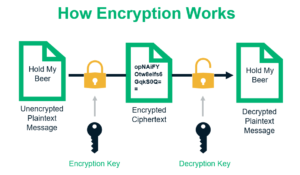
Encryption is the process of transforming plain-text completely into some unreadable format for security. This kind of text is sometimes known as ciphertext. On the contrary, decryption is the reverse process whereby ciphertext is decrypted so that it may reverse back to its original form.
What is Public Key Encryption?
This form of encryption makes use of a public key as well as a private key. It is the public key that encrypts the data whereas it is the private key, that decrypts the data. That’s why this method of encryption is referred to as “asymmetric encryption”. Why? Because the two different keys are utilized.
How Does Public Key Encryption Work?
An algorithm produces a pair of public and private keys. The public key is transmitted to the sender, and the private key is retained by the owner who generated them.
- Once someone wishes to send the encrypted data or crypto, it uses the recipient’s public key to encrypt the message.
- The recipient uses his private key to retrieve and decrypt the data to its original form.
- As the public key is available in public, public key encryption shall be employed in any scenarios where it is mandatory to establish secure communication between entities who have never crossed some encryption keys before.
A third party cannot decrypt the message intercepted without the private key.
This is the sort of encryption applied in blockchains.
What is Private Key Encryption (Symmetric Encryption)?
The key for both encryption and decryption is the same, or symmetric, in private key encryption, and hence it is commonly called symmetric encryption. Obviously, communication cannot begin until both sender and recipient have agreed on the shared key. Because the key must be used both to encrypt and to decrypt, this is often called a symmetric approach, in contrast to the public key encryption approach.
How Private Key Encryption Works?
- Communication cannot occur unless the sender and receiver possess this encrypted private key, securely.
- In this scenario, the sender encrypts his information using the common key.
- The receiver uses the same key to decrypt the message.
- Because both end parties have the same key, private key encryption is faster and more efficient than public key encryption. However, the necessity of having to share the secret key securely in advance beforehand frequently introduces vulnerabilities, especially if the network size is large or that the parties involved are unknown.
Differences Between Public Key and Private Key Encryption
Having now outlined some basics of each, let’s proceed to compare and contrast them on the basis of several key criteria:
1. Use of Keys
Public Key Encryption: Uses two unique keys-public and private. It encrypts using the public key and decrypts using the private key.
Private Key Encryption: The same key is used for encryption and decryption. In the private key encryption process, the sender also shares it with the recipient.
2. Speed and Efficiency
Public Key Encryption: This is the slower approach as it involves lengthy mathematical algorithms for generating a key pair and encrypting data. It is less effective to encrypt huge data.
Private Key Encryption: Better for efficiency and speed. The same key is encrypting and decrypting. It is better for the usage of bulk encryption.
3. Security
Public Key Encryption: Stronger security due to a separate pair of keys. Even if they know the public key, the message cannot be decrypted without the private key.
Private Key Encryption: This is based on how good the protection and sharing of the key are. If somehow the key is compromised at transmission or storage, then the data is easily decrypted by unauthorized individuals.
4. Key Distribution
Public Key Encryption: More feasible for distribution because the public key can be distributed without restrictions. There is no need for a secure channel to exchange keys since only the private key needs to remain secret.
Private Key Encryption: It requires a secure way to transfer the private key between the sender and receiver. This can be viewed as a weakness in case the interceptor somehow gets its hands on the key.
5. Applications
Public Key Encryption: It is suitable for secure communication when parties have not had previous key exchanges. Mostly used when a digital signature by the sender is used for encryption of messages, SSL/TLS certificates, and email encryption.
Private Key Encryption: Best for those scenarios in which both parties have already exchanged keys confidentially. Most people use this to encrypt data transfer in bulk, for instance VPNs, database encryption, and file encryption.
Public Key Encryption Use Cases
Public key encryption is often used between two parties that wish to communicate safely but do not share a common encryption key in advance. Some of its popular use cases include:
SSL Certificate: SSL certificates uses this kind of cryptography to create secure communication between the website and its users.
Email Encryption: Services like PGP uses public key encryption to make sure that only the recipient can read the email.
Private Key Encryption in Practice
Private key encryption is usually applied where efficiency and speed are more important. Some examples include:
File Encryption: This type of encryption is used for files stored in a device or in the cloud. This way, only authorized users with the key can access the data.
Database Encryption: Private key encryption can be used here, especially in cases where encrypting large volumes of data is required.
Combines Use of Public and Private Keys
In many number of systems, both the methods, public key encryption and private key encryption are used together to utilize both the strengths. Hybrid encryption is one commonly used in secure communication protocols. In hybrid encryption:
Public key encryption is used for exchanging symmetric key across sender and recipient.
Once the symmetric key has been shared, private key encryption will then encrypt the actual data, since this mode is fast and efficient.
This method ensures both security and efficiency of encrypting data.
Frequently Ask Questions
What Is the Difference Between Private and Public Key Encryption?
Private and public key encryption are the two main types of asymmetric encryption. In public key encryption there are two keys: one public and one private. The public key is used to encrypt the data so anyone can see it but only the private key can decrypt it so only the intended recipient can read the message. Private key encryption (also known as symmetric encryption) uses one key to encrypt and decrypt the data.
The main difference is the number of keys: public key encryption is asymmetric (two keys) and private key encryption is symmetric (one key).
Do I Encrypt with Public or Private Key?
In public key encryption the public key is used to encrypt the data. When someone wants to send you a secure message they encrypt it with your public key. Once encrypted only your private key can decrypt it so the data is secure and private.
But in digital signatures the process is reversed: you encrypt with your private key to create a signature which can then be verified by others with your public key to ensure authenticity.
What Is the Difference Between Public Key and Private Key in PGP Encryption?
PGP (Pretty Good Privacy) uses both public and private keys for secure communication. The public key is shared with anyone who wants to send an encrypted message to you. The message is encrypted with your public key and can only be decrypted with your private key which you keep secret.
Public and private keys in PGP are public and secret. Public is shared to enable communication, private is kept secret.
Is Private Key More Secure Than Public Key?
Both public and private keys have different uses and security depends on how they are used. Private keys are more sensitive as they are used to decrypt data. If a private key is compromised, encrypted messages can be decrypted and confidential info can be exposed.
Public keys are meant to be public and not a direct security risk if leaked. But private keys must be kept secure and not accessible to others.
What Is an Example of Private Key Encryption?
Private key encryption example is AES. In AES, one key (private key) is used for both encryption and decryption. This is symmetric encryption used for securing sensitive data like file encryption or device to device secure communication.
Another example is DES (Data Encryption Standard) which also uses one key for both encryption and decryption.
Conclusion
Public key encryption is stronger in security and ideal for establishing secure communication between parties who haven’t exchanged keys prior to this. However, it is slower and less efficient for the encryption of large amounts of data.
Private key encryption, on the other hand is faster and more efficient but requires secure key exchange.
Key differences between public and private key encryption provide an understanding for the purposes of selecting both public and private key methods, depending upon the particular requirements and use cases, in order to provide informed decisions. Quite often, a combination of both ways will provide an ideal balance between security and efficiency.