What is a Crypto Wallet

Crypto wallets are software that helps you secure your private keys and access your blockchain address, where the cryptocurrencies are present. These wallets usually come as independent software (hot wallet) or software present inside a pre-programmed hardware device (cold wallet).
This article provides a brief overview of crypto wallets, their workings, types, and the best practices for securing them.
How Do Crypto Wallets Work?
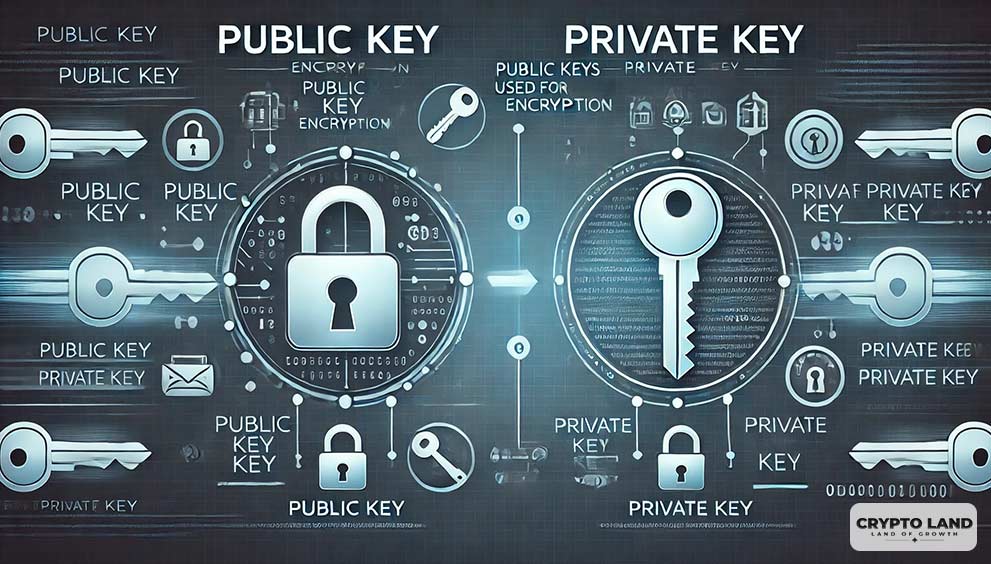
Every blockchain has several addresses that store the crypto. These addresses have two things attached to them: the first is their public address, which is the address you send others to receive crypto, and the second is the private key, which is the password through which you access these blockchain addresses.
Since blockchains are anonymous, they do not have a recovery method. So, if you lose your private key, your crypto is gone forever. Further, private keys are composed of multiple alphanumeric characters, which makes them difficult to remember.
A crypto wallet is software that lets you safely store private keys from multiple blockchains so that you have at least a way to secure your crypto in case you forget them.
Types of Crypto Wallets
There are two types of crypto wallets, and they depend on how they are made to operate.
The first and most common category is software wallets, which are software installed on mobile phones or laptops.
The second category is the hardware wallet, which can only be used when it is connected to your phone or the internet.
Hot Wallets
Hot wallets are made for frequent daily access and for storing crypto that you need for daily activities like paying gas fees, swapping crypto, or moving tokens to and from the exchanges.
Here, a piece of software with all the private keys to your blockchain addresses is installed on your phone or computer.
Software or hot wallets can exist independently, such as the MetaMask wallet app and Trust Wallet app. They can also be embedded plug-ins in other software, such as web browser extensions.
A few social media apps like Telegram also have embedded software wallets in them.
These wallets are further classified as custodial and non-custodial wallets.
Custodial wallets are those that keep the private key with itself but let you recover your access in case you forget your keys. These wallets are often found as exchange wallets with exchanges like Binance, Coinbase, and OKX. These wallets are good for beginners and do not require any expertise to operate.
Non-custodial wallets give users full access to their wallets. Here, the users are responsible for maintaining their private keys. However, these wallets also provide a recovery method through seed phrases, which are a set of words that help you recover your wallet in case you forget its password.
Examples of non-custodial wallets include MetaMask, Trust Wallet, Math Wallet, Enjin Wallet, and Guarda Wallet.
Cold Wallets
Cold wallets are usually designed for infrequent access and long-term storage. These wallets are inside their hardware and can be disconnected from the internet to prevent non-sanctioned access.
When required, such wallets can be connected to the Internet or a mobile app, which allows them to perform usual transactions. Though these wallets are relatively safe, they don’t guarantee full safety.
Examples of cold wallets are Ledger NanoX, Safepal Wallet, Ellipal Titan, etc.
Best Practices for Safeguarding Your Crypto Wallet
Crypto wallets are anonymous and often only have a single layer of authentication. Though there is a recovery phrase for these wallets, however for all ordinary purposes, just knowing the wallet password is enough for hackers to steal your crypto.
Here are some best practices to safeguard your wallet, whether hardware or software, so you can stay much safer.
- Always ensure that you never reveal your private keys, wallet password, or secret recovery phrases to anyone, whether intentionally or unintentionally.
- Always write private keys and store them in a place that no one can access except you.
- Never share your wallet keys, even with yourself, through social media or any messaging app.
- Try to keep your personal and professional wallets separate from each other, preferably on different devices.
- Make sure you update the firmware of your hardware wallets so that they function without any hiccups.
- Hardware wallets should be used as sparingly as possible to prevent any hack or stealing incident.
Also : What is Crypto Market Cap?
Frequently Asked Questions
Which crypto wallet is best?
A custodial wallet is best for new users. Hot wallets like Trust Wallet are best for frequent users. Cold wallets provide the best features for long-term investors.
Can I transfer money from my crypto wallet to a bank account?
You need to encash your crypto and sell it on a CEX to obtain cash, which can be transferred to your bank account.
Can you buy crypto through a bank and store it in a wallet?
Yes, you can buy crypto and pay from your bank account via P2P, net banking, or credit card. Alternatively, several banks directly sell you crypto. After the purchase, you can simply send your crypto to your wallet.
Who can see my crypto wallet?
Your crypto wallet, funds, and pass keys should only be accessible to you. But, on a blockchain explorer, you can view any wallet address (but not control) and see its funds, transfers, and other details.


















![Top Altcoins in October [2024] You Should Look Out For 19 Top Altcoins in October [2024] You Should Look Out For](https://cryptolandoff.com/wp-content/uploads/2024/10/Top-Altcoins-in-October-2024-You-Should-Look-Out-For.jpeg)